Quick Summary:
Food delivery app security best practices involves robust authentication, data encryption, secure payment processing, regular audits, data privacy, API security, fraud detection, and employee training. Implementing these best practices protects sensitive information, enhances user trust, and ensures operational efficiency, helping your app succeed in a competitive market.
According to the report, the food delivery industry expected to surpass $165 billion by 2029, the security of food delivery apps like Uber Eats, DoorDash, and Grubhub has never been more critical. Sensitive data privacy and fraud prevention are critical given that customers are depending more and more on these platforms for their daily meals.
This guide explores essential food delivery app security best practices, providing strategies to shield your platform from cyber threats and vulnerabilities. In an industry that is always growing, you may foster trust and loyalty among your clients by implementing these best practices and providing a safe & secure understanding for them.
Essential Security Best Practices for Food Delivery Apps
Convenience shouldn’t come at the cost of security! While food delivery apps have transformed how we eat, protecting user data, financial information, and even food safety requires a multi-layered approach. From robust authentication and secure transactions to vigilant app maintenance, let’s explore how to build a safe and delicious food delivery app using security best practices:
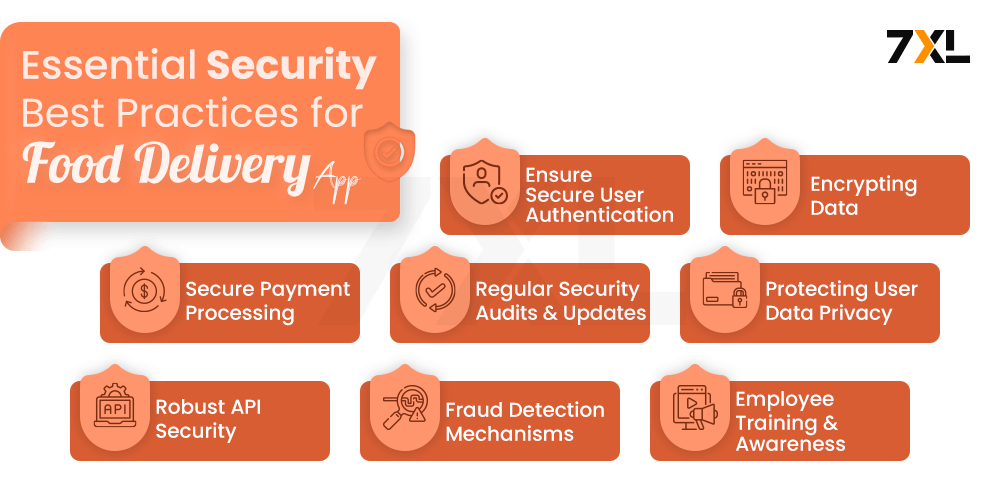
1. Secure User Authentication
Ensuring robust user authentication involves creating a seamless yet secure login process. Striking a balance between security & user experience is crucial, as overly complex authentication processes can frustrate users and lead to abandonment.
Multi-Factor Authentication (MFA):
Implementing By demanding that users submit a minimum of two verification variables in order to get access, MFA adds an additional level of protection. Thus, even in the event that the password entered by the user is compromised, the likelihood of unwanted access is greatly decreased.
Examples of MFA include a password plus a fingerprint scan, a code sent to the user’s phone, or an authentication app. The reason MFA works so well is that it combines the user’s knowledge (password), possessions (phone), and identity (biometric verification).
Strong Password Policies:
impose strict guidelines on passwords; for example, mandate that they have a mix of capital and numeric characters. Recommend that users refrain from using popular passwords and update them on a regular basis. Implementing features like password strength meters can help users create more secure passwords. Additionally, consider educating users about the importance of unique passwords for different services to minimize the risk of credential stuffing attacks.
2. Data Encryption
Encrypting data is a fundamental security practice that protects user privacy and builds trust.A platform that puts an emphasis on protecting users’ personal information is more likely to draw in users.
End-to-End Encryption:
Secure sensitive data both in transit & at rest to prevent unauthorized access. This ensures that even if data is intercepted, it cannot be read without the decryption key. Use strong encryption algorithms like AES (Advanced Encryption Standard) for robust security. End-to-end encryption protects sensitive information from the moment it leaves the sender until it reaches the intended recipient, making it unreadable to anyone who intercepts it.
SSL/TLS Protocols:
Use SSL/TLS protocols to secure data exchanged between the app and the server. This protects data from being intercepted and tampered with during transmission. Always use the latest versions of these protocols to mitigate known vulnerabilities. Implement HTTPS across your entire platform to ensure all communications are encrypted.
3. Secure Payment Processing
Securing payment processing is vital for maintaining customer trust and preventing financial losses. When use your app, users should have peace of mind knowing that their financial details are secure.
PCI DSS Compliance:
To safeguard payment information, make sure your app conforms with the Payment Card Industry Data Security Standard (PCI DSS). This entails protecting cardholder data with encryption, keeping networks safe, putting robust access control mechanisms in place, and routinely testing and monitoring networks. Observing PCI DSS compliance contributes to fraud and data breach prevention.
Tokenization:
To minimize the danger of data breaches, replace critical payment information with a unique identifier (token). Without disclosing real payment information, tokens can be utilized for transactions. Because of this, hackers can’t use stolen info. Since sensitive information is never directly stored or transmitted, tokenization offers an additional degree of protection.
Fraud Prevention Tools:
Implement tools to detect and prevent fraudulent transactions. These can include machine learning algorithms that identify suspicious patterns, velocity checks to limit the number of transactions in a short period, and address verification systems (AVS) to verify the legitimacy of transactions.
4. Regular Security Audits and Updates
Regular security audits & updates are important for maintaining a secure app environment. Staying proactive helps prevent potential security breaches and ensures your app is always protected against the latest threats.
Frequent Security Audits:
Conduct regular security audits to identify and fix vulnerabilities. This proactive approach helps in mitigating potential threats before they can be exploited. Use both automated tools and manual reviews to ensure comprehensive coverage. Regular audits should include vulnerability assessments, penetration testing, and code reviews.
Timely Updates:
Utilize the most recent security fixes and updates to keep your program and its dependencies current. Outdated software can be a gateway for attackers to exploit known vulnerabilities. Automate updates where possible to ensure timely implementation. Regularly update third-party libraries and frameworks to mitigate risks from external dependencies.
Patch Management:
Enable all systems and apps to receive the most recent security fixes by putting in place a strong patch management procedure. This includes operating systems, databases, middleware, and application software. Develop a process for identifying, testing, and deploying patches in a timely manner.
5. Protecting User Data Privacy
Protecting user data privacy is crucial for building and maintaining user trust. Adopting transparent and ethical data handling practices can enhance your app’s reputation and compliance with regulatory requirements.
Privacy Policies:
To gather and utilize user data, get their consent and clearly state your policy regarding data protection. Along with ensuring adherence to data protection laws like the CCPA and GDPR, transparency fosters confidence. Make users’ access to your privacy policy simple. It is advisable to periodically assess and revise your privacy policy to align with evolving regulations or modifications to data handling procedures.
Minimal Data Collection:
Collect only the necessary data required for app functionality to minimize the risk of data breaches. The less data you store, the less there is to protect. Regularly review and purge unnecessary data to reduce potential risks. Adopt data minimization principles to limit data collection to what is strictly necessary for the app’s operation.
Data Anonymization:
Where possible, anonymize user data to protect their identity. This involves removing personally identifiable information (PII) from datasets, making it impossible to link data back to individual users. Anonymization helps protect user privacy while still allowing for useful data analysis.
User Rights Management:
Provide users with control over their data, including options to access, update, and delete their information. Add functionality that lets users adjust their preferences & privacy settings. Ensure compliance with regulations that grant users specific rights over their personal data.
6. Robust API Security
Ensuring robust API security is essential for protecting the integrity of your app and its data. APIs are a critical component of modern applications, and securing them helps prevent potential vulnerabilities and attacks.
API Gateway:
Use an API gateway to manage and secure API traffic. This helps in controlling access, enforcing policies, and monitoring API usage. An API gateway can also provide features like load balancing, rate limiting, and threat detection. Ensure that all API endpoints are protected by strong authentication and authorization mechanisms.
Rate Limiting:
Utilize rate limiting to prevent abuse & attacks on your API. This controls the number of requests a user can make in a given period, protecting against denial-of-service attacks and ensuring fair usage of resources. Rate limiting helps prevent API misuse and ensures the stability of your services.
OAuth and OpenID Connect:
Use OAuth and OpenID Connect for secure and standardized authentication and authorization. Without disclosing their login information, users can safely allow other apps to access their resources with the help of these protocols.
Input Validation and Sanitization:
Validate and sanitize all inputs to APIs to prevent injection attacks and other common security vulnerabilities. Use parameterized queries and input validation libraries to ensure data integrity and security.
API Monitoring and Logging:
Continuously monitor and log API activity to detect and respond to security incidents. Implement logging mechanisms that capture detailed information about API requests and responses. Regularly review logs for suspicious activities and anomalies.
Interested to develop a standout food delivery app?
At 7xcel, our on-demand food delivery app development services empower food business owners to rapidly enhance brand visibility and boost sales.
7. Fraud Detection Mechanisms
Protecting your company and consumers from financial losses requires the implementation of strong fraud detection systems. A proactive approach to fraud prevention helps maintain user trust and ensures the security of your platform.
Machine Learning Algorithms:
In real time, identify and stop fraudulent activity with machine learning algorithms. By seeing odd trends and flagging questionable transactions, these algorithms enable quick inquiry and action. Models for machine learning can be trained on past data to identify trends and anticipate dishonest behavior.
Transaction Monitoring:
Continuously monitor transactions for suspicious patterns and behaviors. Immediate detection and response can prevent fraud from escalating. Implement automated systems that can halt transactions and alert security teams to potential issues. Real-time monitoring helps identify and mitigate fraud risks promptly.
Behavioral Analytics:
Use behavioral analytics to identify abnormal user behavior that may indicate fraud. Track metrics such as login times, IP addresses, device information, and transaction amounts to detect deviations from normal patterns. Behavioral analytics provides insights into user activities and helps identify potential threats.
Multi-Layered Fraud Prevention:
Implement a multi-layered approach to fraud prevention that combines machine learning, transaction monitoring, and behavioral analytics. This comprehensive strategy enhances the detection and prevention of fraudulent activities. Multi-layered security measures provide robust protection against evolving fraud tactics.
Collaboration with Financial Institutions:
Partner with payment processors and financial institutions to exchange knowledge and best practices around preventing fraud. This partnership can enhance your ability to detect and respond to fraudulent activities. Leveraging the expertise of financial institutions helps strengthen your fraud prevention efforts.
8. Employee Training and Awareness
A thorough security strategy must include employee awareness and training. Employees with the necessary training can recognize and address security risks, strengthening your company’s overall security stance.
Regular Training:
To keep staff members up to date on the newest security dangers and best practices, regularly provide security training. Educated employees are your first line of defense against security breaches. Include phishing simulations and other practical exercises in your training programs. Regular training ensures employees are aware of evolving threats and can effectively respond to security incidents.
Access Control:
Limit employee access to sensitive information based on their roles and responsibilities.Internal threats are less likely to occur when the least privilege principle is put into practice. To effectively manage permissions, apply role-based access control, or RBAC. Policies pertaining to access control should be periodically reviewed and revised to take into account modifications to employee roles and responsibilities.
Security Awareness Campaigns:
In order to foster a security-conscious culture within your company, run security awareness programs. Convey the value of security procedures through emails, posters, and other forms of communication. Awareness campaigns help keep security top of mind for employees.
Incident Response Training:
To guarantee a prompt and efficient reaction to security incidents, provide staff with incident response training. In order to evaluate and enhance incident response capabilities, regularly conduct exercises and simulations. Reducing the effect of security breaches requires preparation.
Secure Development Training:
Provide secure development training to developers to ensure they follow best practices for coding securely. Topics should include secure coding techniques, common vulnerabilities, and secure software development lifecycle (SDLC) processes. Secure development training helps prevent vulnerabilities in the application code.
Conclusion
Securing your food delivery app like Uber Eats, DoorDash, and Grubhub is not just about protecting data; it’s about maintaining trust and ensuring a seamless user experience. By implementing these best practices, you can safeguard your app against potential threats and create a secure environment for your users. Stay proactive and vigilant in your approach to security, and your app will thrive in the competitive food delivery market.
By focusing on secure user authentication, data encryption, secure payment processing, regular security audits, user data privacy, robust API security, fraud detection mechanisms, and employee training, you can build a secure food delivery app that meets the highest standards of security and user trust.