Quick Summary:
Securing your grocery delivery app is crucial to protect user information and build trust with your customers. With the rise of online shopping, it’s more important than ever to ensure your app is safe from cyber threats. In this blog, we will cover straightforward steps to secure your grocery delivery app and keep your customers’ data protected.
In the booming on-demand food delivery market, securing your grocery app is crucial for building trust and staying competitive. According to a report by Allied Market Research, global sales of mobile applications for food delivery were valued at $6,752.32 million in 2020, with the market expected to grow at a CAGR of 25% from 2021 to 2030, reaching $62,836.97 million.
With this rapid growth, robust security measures are more important than ever to protect against potential cyberattacks. This guide covers essential tactics for safeguarding your app, from strong authentication to legal compliance, ensuring your platform remains safe, trustworthy, and poised for long-term success.
Understanding the Security Landscape
Before implementing specific security measures, it’s essential to understand the broader security landscape that affects grocery apps. This includes recognizing current threats, challenges, and regulatory requirements:
Current Threats
Cyber Attacks
- Phishing: Deceptive messages trick users into sharing sensitive information.
- Malware: Malicious software can infect devices and servers, causing data breaches.
- Man-in-the-Middle (MitM) Attacks: Attackers intercept communications to steal or alter data.
Data Breaches
Financial loss, harm to one’s reputation, and legal problems may result from user information, such as addresses and payment details, being made public.
Identity Theft
It is possible to impersonate someone using stolen personal information of users, leading to unauthorized transactions and privacy violations.
Challenges
Balancing Security and Usability
In order to prevent annoyance and lower adoption, security solutions must safeguard the app without sacrificing the user experience.
Evolving Threats
New threats emerge regularly, requiring continuous monitoring, updates, and a proactive approach to security management.
Resource Constraints
Implementing security measures can be resource-intensive, demanding strategic planning and prioritization within limited budgets.
Regulatory Requirements
GDPR (General Data Protection Regulation)
Requires obtaining user consent, providing data access and deletion rights, and reporting breaches within 72 hours.
CCPA (California Consumer Privacy Act)
Grants rights to know, delete, and opt-out of the sale of personal data for California consumers.
Industry Standards
PCI DSS (Payment Card Industry Data Security Standard)
guarantees that credit card information is processed, stored, and transmitted in a secure manner.
OWASP (Open Web Application Security Project)
Provides best practices for securing web applications and mitigating common vulnerabilities.
Importance of a Security-First Mindset
Adopt a proactive security approach by:
- Implementing Measures Early: Integrate security during app development.
- Continuous Improvement: Regularly update security protocols.
- User Education: Inform users about security best practices.
Understanding the security landscape helps developers anticipate threats and implement effective security measures, ensuring a safe and reliable developing a successful grocery app.
Comprehensive Security Measures for Protecting Grocery App
While grocery apps provide convenient shopping, they also face significant risks from online threats. To keep the app secure and maintain user trust, it’s essential to implement strong security measures, including user authentication, data encryption, secure payment gateways, and regulatory compliance.
Working with a specialized Grocery App Development Company can ensure these protections are effectively integrated, offering a safer and more reliable platform for users.
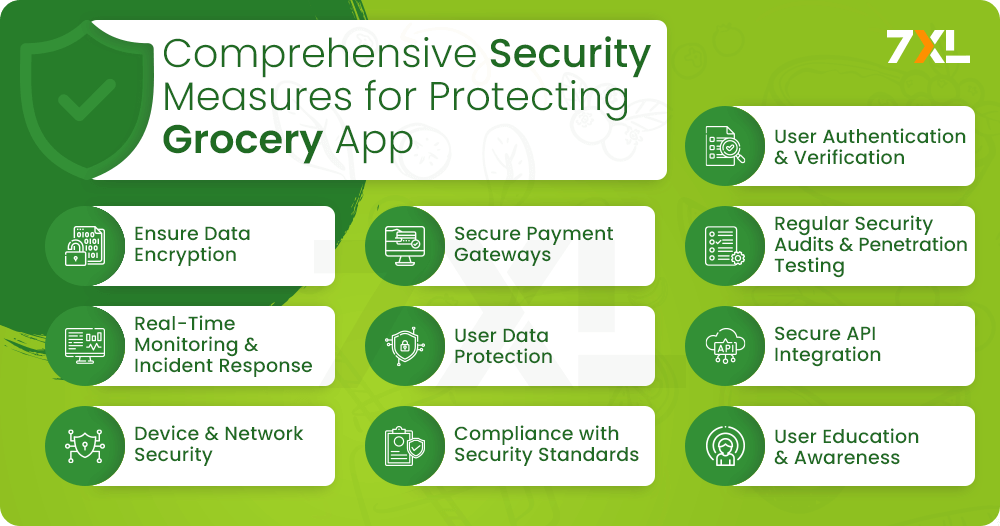
1. User Authentication and Verification
Strong Password Policies
Implementing strong password policies is essential for securing user accounts. Ensure that passwords:
- Need a combination of digits, special characters, and capital and lowercase letters.
- Have a minimum length, typically at least 8-12 characters.
- Encourage users to change their passwords periodically, such as every 3-6 months.
- Avoid using easily guessable information, such as common words, birthdays, or simple sequences (e.g., “12345”).
Two-Factor Authentication (2FA)
2FA adds an additional layer of security by mandating two forms of verification:
- Something the user knows (password).
- Something the user has it can be a mobile device to receive a one-time code or a hardware token.
Even in the event that the password is compromised, the likelihood of unwanted access is greatly decreased by combining these two considerations.
2. Data Encryption
SSL/TLS Protocols
Secure Socket Layer & Transport Layer Security protocols are crucial for encrypting data transmitted between the app and the server:
- Ensure that all communications use HTTPS, which incorporates SSL/TLS, to prevent data interception.
- Regularly update SSL/TLS certificates to maintain security.
End-to-End Encryption
Data is guaranteed to stay encrypted from the sender to the recipient with end-to-end encryption:
- Data is shielded from interception and manipulation during transmission by being encrypted and only readable by the sender and receiver.
3. Secure Payment Gateways
PCI DSS Compliance
The Payment Card Industry Data Security Standard sets requirements for secure processing, storage, and transmission of credit card information:
- Use payment gateways that comply with PCI DSS to protect cardholder data.
- Regularly audit your payment processing systems to ensure compliance.
Tokenization
Tokenization swaps the sensitive payment data with unique identifiers (tokens):
- Tokens are meaningless outside the payment system, reducing the risk of data breaches.
- Store tokens instead of actual payment information to enhance security.
4. Regular Security Audits and Penetration Testing
Regular Security Audits
To find and address vulnerabilities, do routine security audits:
- Affirm secure coding standards by doing code reviews.
- To find possible security holes, conduct vulnerability assessments.
- Ensure compliance with security standards and regulations.
Penetration Testing
Penetration testing involves ethical hackers simulating attacks on your app:
- Determine whether weaknesses malevolent attackers could exploit
- Address and fix these vulnerabilities before they can be exploited.
5. Real-Time Monitoring and Incident Response
Real-Time Monitoring
Implement tools to monitor your app and detect suspicious activities in real-time:
- Monitor user behavior for anomalies.
- Track transaction patterns for signs of fraud.
- Detect unauthorized access attempts and respond promptly.
Incident Response Plan
To address security breaches, create a thorough incident response plan:
- Identify the breach quickly and assess the damage.
- Contain the breach to prevent further damage.
- Eradicate the threat and remove compromised elements.
- Recover systems and restore normal operations.
- Communicate with affected users and regulatory authorities as required.
6. User Data Protection
Data Minimization
Collect only the data necessary for the app to function:
- Avoid storing sensitive information unless absolutely necessary.
- Implement policies to delete unnecessary data promptly.
Secure Data Storage
Ascertain the secure storage of all user data:
- Use encryption to protect data at rest.
- Employ secure storage solutions to prevent unauthorized access and data breaches.
7. Secure API Integration
API Security Best Practices
Secure all API endpoints with strong authentication and authorization mechanisms:
- Implement API keys and tokens to control access.
- Use OAuth or similar frameworks for secure authorization.
- Rate limit API requests to prevent abuse and denial-of-service attacks.
Regular API Audits
Conduct regular audits of your APIs:
- Ensure they comply with security best practices.
- Identify and fix vulnerabilities in API integrations.
8. Device and Network Security
Device Integrity Checks
Ensure your app performs integrity checks to detect compromised devices:
- Prevent the app from running on rooted or jailbroken devices.
- Restrict functionality if a compromised device is detected.
Secure Network Communication
Use secure methods to protect data transmission between the app and backend servers:
- Implement Virtual Private Networks (VPNs) for secure communication.
- Use firewalls to filter and monitor network traffic, blocking unauthorized access.
9. Compliance with Security Standards
GDPR and CCPA Compliance
Make sure your software conforms with laws pertaining to data protection, like the CCPA and GDPR:
- Get the user’s express consent before gathering their personal information.
- Allow users to access, modify, and delete their data.
- Ensure data breaches are reported to authorities and affected users within the required timeframe.
Regular Compliance Audits
Evaluate compliance with applicable security standards and laws on a regular basis by conducting audits:
- Keep the app up-to-date with the latest security requirements.
- Regularly review and update your compliance practices.
10. User Education and Awareness
Security Awareness Programs
Educate users about the crucialness of security & best practices:
- Teach users how to recognize phishing attempts.
- Encourage the use of strong passwords.
- Provide tips on safeguarding personal information.
In-App Security Tips
Offer users security tips and reminders within the app:
- Display security best practices during onboarding.
- Provide periodic reminders to update passwords and enable 2FA.
- Highlight new security features and how to use them effectively.
By following these detailed steps, you can significantly enhance the security of your grocery app, protecting both user data and business operations from potential threats.
Interested to develop a standout grocery delivery app?
Revamp your grocery business with 7xcel’s cutting-edge app development, extending your influence online.
How to Ensure Operational Reliability and Resilience of Grocery App?
Beyond securing user data and transactions, it’s crucial to implement measures that ensure the operational reliability and resilience of your grocery app. This includes:
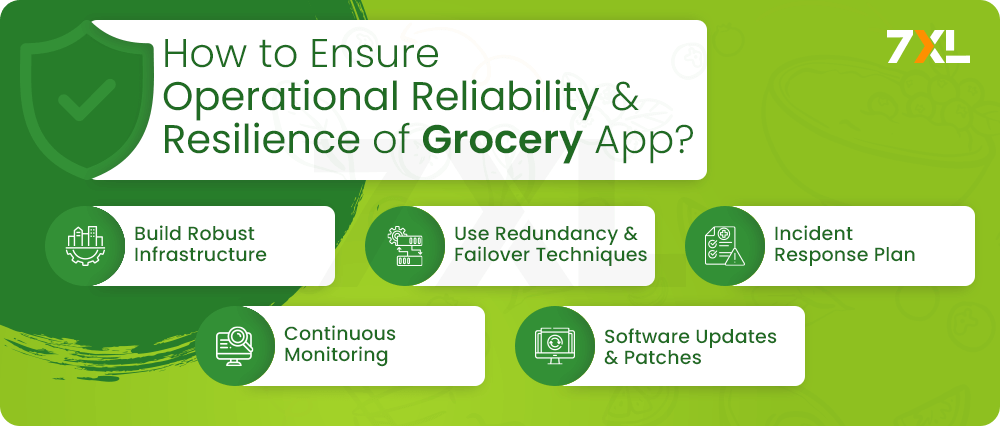
Robust Infrastructure
Build your app’s infrastructure on a secure and scalable cloud platform, such as AWS or Google Cloud, that offers built-in security features and the ability to quickly scale resources as needed. According to a report by MarketsandMarkets, The global market is predicted to expand at a CAGR of 17.5% from $371.4 billion in 2020 to $832.1 billion by 2025.
Redundancy and Failover
Use failover and redundancy techniques to make sure your app can survive network outages, hardware malfunctions, and other hiccups without reducing service availability. A study by the Uptime Institute found that the average cost of a data center outage is $740,357.
Incident Response Plan
In the event of a system breakdown or security breach, develop a thorough incident response plan that specifies what needs to happen. Processes for incident identification, containment, investigation, and recovery should all be included in this strategy. In general, it takes 280 days to find and stop a data breach, according to a Ponemon Institute analysis.
Continuous Monitoring
To quickly identify & address performance problems, security breaches, or any other abnormalities, put continuous monitoring systems into place. This can include logging, alerting, and automated remediation mechanisms. A study by the Ponemon Institute found that organizations with a strong security monitoring program experience 32% fewer data breaches .
Software Updates and Patches
Regularly update your app’s software, including the operating system, frameworks, and third-party libraries, to address security vulnerabilities and ensure that your app remains secure against emerging threats. According to a report by Verizon, In 60% of cases, there existed a vulnerability for which there was a fix but it was not used.
Compliance and Regulatory Considerations for the Grocery App
It is vital to adhere to pertinent industry norms and standards in order to preserve the security and dependability of your grocery app. Among the crucial factors for compliance are:
Data Protection Regulations
To guarantee the secure management of user data, abide by data protection laws such as the California Consumer Privacy Act (CCPA) and the General Data Protection Regulation (GDPR). Fines for noncompliance with GDPR can reach up to €20 million, or 4% of worldwide revenue.
Payment Card Industry Data Security Standard
To guarantee the safe handling and preservation of credit card information, comply with PCI DSS regulations. Non-compliance with PCI DSS can lead to fines, penalties, and the inability to process credit card transactions .
ISO 27001
If you want to show that you are committed to strong security measures, make sure your security procedures follow the ISO 27001 standard, which is the international standard for ISMS. Achieving ISO 27001 certification can enhance customer trust and open up new business opportunities .
HIPAA
HIPAA compliance is necessary if your app handles sensitive health data in order to safeguard user information. Penalties for HIPAA violations range from $50,000 to $1.5 million annually, maximum amount per event.
FISMA
For apps that handle financial data, comply with the Federal Information Security Management Act (FISMA) to meet the security requirements of federal agencies. Failure to comply with FISMA can lead to the loss of government contracts and funding .
Conclusion
Implementing comprehensive security features in your grocery delivery app is essential to protect users and their data. By focusing on user authentication, data encryption, payment security, real-time tracking, secure APIs, and user verification, you can create a safe and trustworthy environment for both users and drivers. Regular security audits and user education further enhance your app’s security posture.








